Blog Overview
- Azure Point to Site Configuration
- Azure Virtual Network Gateway Configuration
- AWS Site to Site VPN Configuration
- Azure Site-to-Site VPN Configuration
- Final Overview
- AWS Site to Site VPN/BGP Troubleshooting
- Azure Site to Site VPN/BGP Troubleshooting
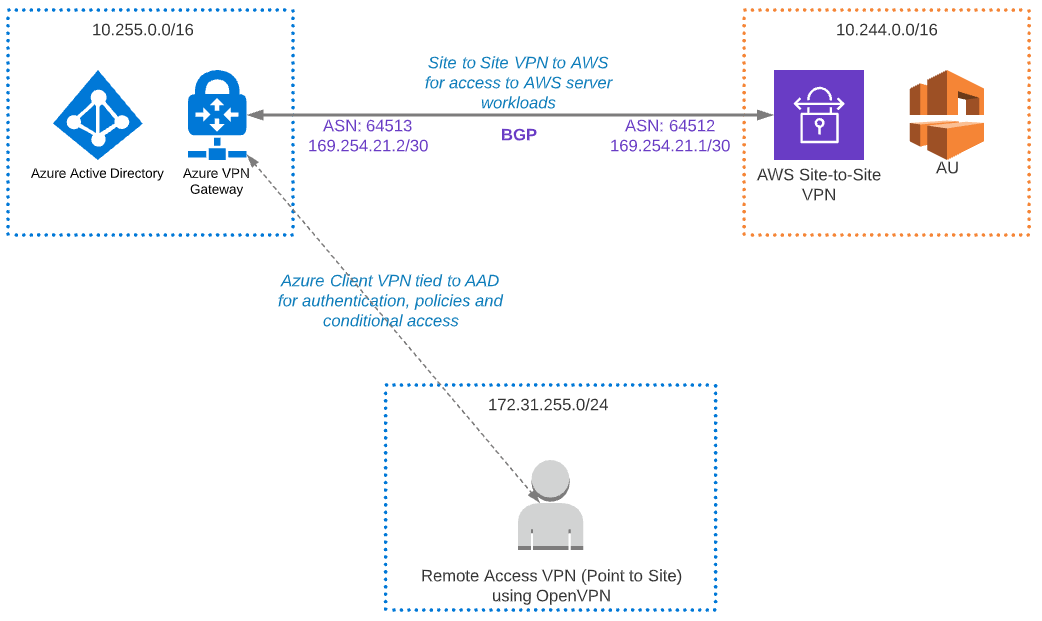
As pictures speak louder than words, refer to the diagram below for the end state architecture.
- At the end of the first section (Azure Point to Site Configuration) you should be able to connect to Azure VPN with clients and authenticate via Azure AD.
- Once everything is configured, VPN clients will be able to access AWS resources through Azure.
Azure Point to Site Configuration
- More information: VPN Gateway: VPN Gateway: Azure AD tenant for P2S VPN connections: Azure AD authentication | Microsoft Docs
- I didn’t have to add any routes manually to clients (although I only tested in Windows 10)
1. Create a VNET (10.255.0.0/16)
2. Create a Virtual Network Gateway (VpnGw1 SKU, as the Basic SKU is not supported for OpenVPN) with a Gateway Subnet (10.255.0.0/24)
3. Create an Enterprise Application to enable Azure VPN Client to authenticate to Azure AD
For most public regions, you can use the URL below to create the enterprise application (refer to the URL above for other regions). Ensure the account you log in with has adequate permissions in Azure AD.
https://login.microsoftonline.com/Azure AD Tenant ID/oauth2/authorize?client_id=41b23e61-6c1e-4545-b367-cd054e0ed4b4&response_type=code&redirect_uri=https://portal.azure.com&nonce=1234&prompt=admin_consent
4. Grant Application Access
Add the users/groups who you want to have access to the ‘Azure VPN’ Enterprise Application in Azure AD.
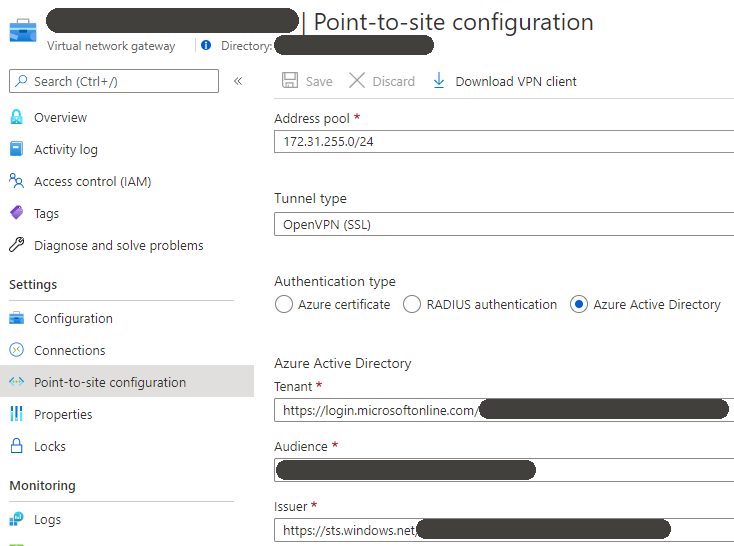
5. Configure ‘point to site configuration’ on the Virtual Network Gateway
The Azure Active Directory (tenant, audience & issuer) settings come from the application created in step 3.
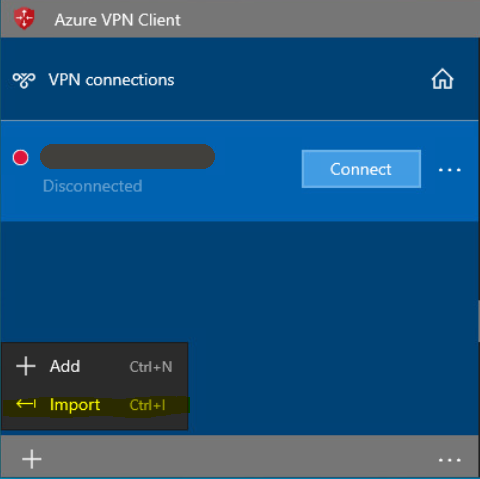
6. Client configuration
Download the XML file from the ‘Point-to-site configuration’ screen (screenshot above, ‘Download VPN Client’), install the Azure VPN client from Microsoft Store and then import the XML file.
Azure Virtual Network Gateway Configuration
The Virtual Network Gateway has to be created in Azure to get the public IP, which is then used to complete the AWS configuration, before returning to Azure.
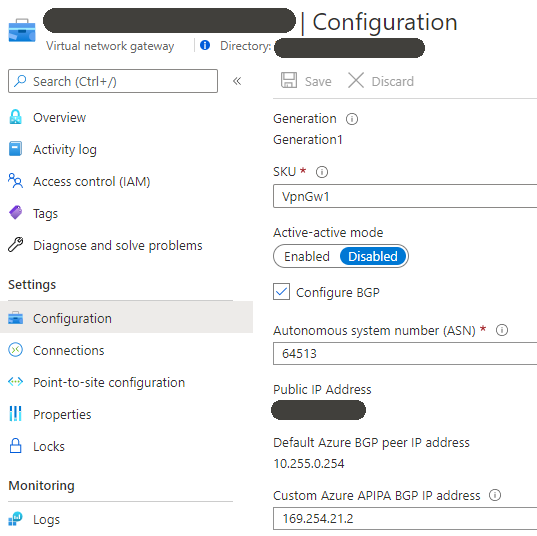
1. Configure the Virtual Network Gateway for Site to Site VPN to AWS
- Tick ‘Configure BGP’
- ASN: Azure ASN Number
- BGP ASN Restrictions: https://docs.microsoft.com/en-us/azure/vpn-gateway/vpn-gateway-bgp-overview
- APIPA BGP IP address: Azure BGP Peer Address
- APIPA IP Restrictions: https://docs.microsoft.com/en-us/azure/vpn-gateway/bgp-howto
AWS Site to Site VPN Configuration
1. Create VPC (10.244.0.0/16)
2. Create Subnet (10.244.1.0/24) in VPC
3. Create Virtual Private Gateway and attach it to the above VPC
- I let AWS create the ASN and it used the default value of 64512. If you want to use a custom ASN, this is where you configure it.
- Make sure to also enable ‘route propagation’ on the relevant route table.
4. Create Customer Gateway
Before you can do this, you’ll need to create the Virtual Network Gateway in Azure (see Azure section above) and get the public IP.
- Routing: Dynamic
- BGP ASN: Azure BGP Peer IP Address
- IP Address: Public IP of the VPN endpoint in Azure (Can get it from the VNG Overview Page)
The rest of the settings can be left as the defaults (you don’t need to select a certificate ARN).
5. Create Site-to-Site VPN Connection
- Target Gateway Type: Virtual Private Gateway
- Virtual Private Gateway: < created above >
- Customer Gateway: Existing
- Customer Gateway ID: < created above >
- Routing Options: Dynamic
- Tunnel Inside IP Version: IPv4
- Local IPv4 Network CIDR: < Leave blank as we will use BGP >
- Remote IPv4 Network CIDR: < Leave blank as we will use BGP >
- Inside IPv4 CIDR for Tunnel 1: 169.254.21.0/30
- AWS asks for a network address here, rather than IP (unlike Azure) and the AWS tunnel will consume the first usable IP (.1 in this case)
- Pre-Shared Key for Tunnel 1: PSK for the VPN connection, must match Azure side.
Azure Site-to-Site VPN Configuration
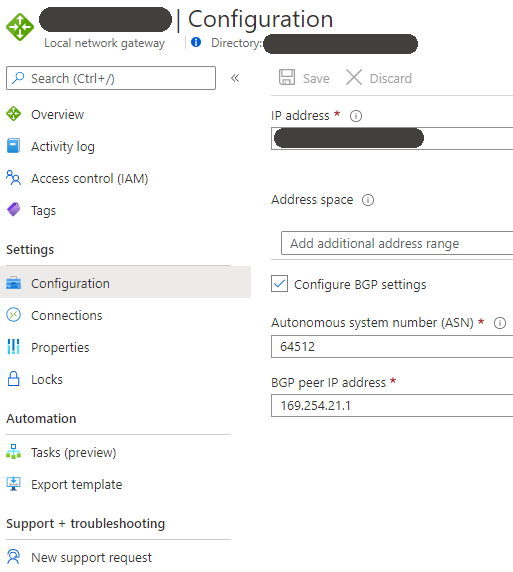
1. Configure the Local Network Gateway
Before you can do this, you’ll need to create the site-to-site VPN in AWS (see AWS section above) and get the public IP.
- IP Address: Public IP of the VPN endpoint in AWS
- Address Space: < Leave blank as we will use BGP >
- ASN: AWS ASN Number
- BGP Peer IP: AWS BGP Peer IP Address
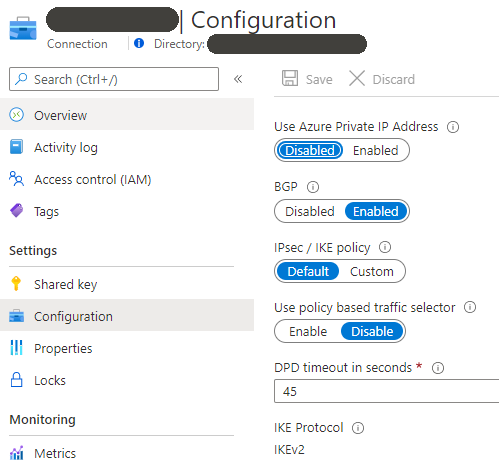
2. Configure the Site to Site VPN Connection
- Connection Type: Site-to-site (IPsec)
- Virtual Network Gateway: < created above >
- Local Network Gateway: < created above >
- Shared key (PSK): PSK for the VPN connection, must match AWS side.
- Tick ‘Enable BGP’
- IKE Protocol: IKEv2
Final Overview
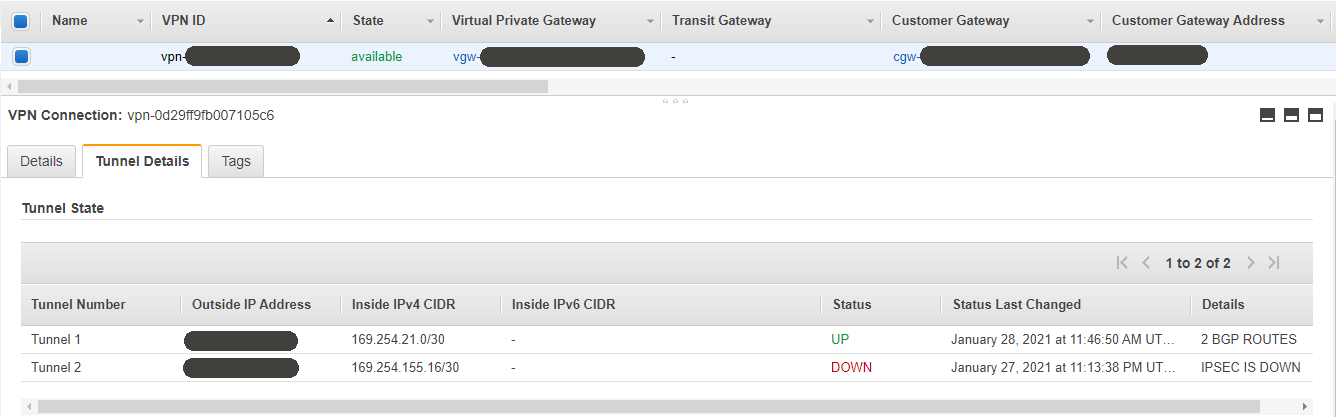
At this point the tunnel should come UP. Tunnel 2 is showing as down as I only configured a single link, but two can be configured for redundancy. See the AWS troubleshooting section for a bit more information.
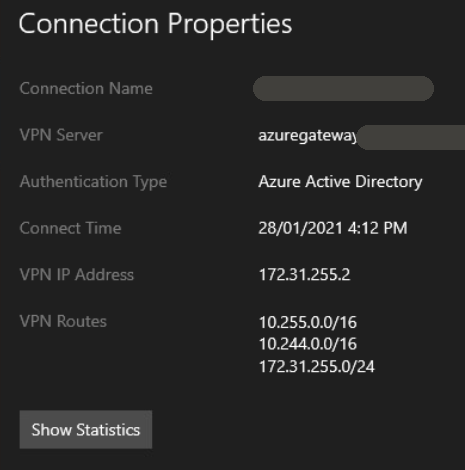
Azure VPN Client showing learned routes via BGP.
AWS Site to Site VPN/BGP Troubleshooting
If the tunnel status is showing DOWN but detail shows IPSEC IS UP, it means VPN is up but the BGP peering has not succeeded. See ‘Azure Site to Site VPN/BGP Troubleshooting’ for more information.
Azure Site to Site VPN/BGP Troubleshooting
There were three useful commands in Azure PowerShell I used to troubleshoot BGP issues. You need to specify the Resource Group name, Virtual Network Gateway name and for the top two commands you need to put in the BGP peer (169.254.21.1).
az network vnet-gateway list-advertised-routes az network vnet-gateway list-bgp-peer-status az network vnet-gateway list-learned-routes
You can also enable logging to Log Analytics, where you can then view any related events, Azure VPN Gateway: Configure alerts on diagnostic resource log events | Microsoft Docs. Once configured, the query below will list all routing related query logs in Log Analytics.
AzureDiagnostics | where Category == "RouteDiagnosticLog"

Great guide Gregor!
unblocked a few gaps for me
I’m wondering if you tried an active/active config?
I set this up and noted aws tunnel 1 receiving the route and traffic traversing ok
as a test i changed when the PSK on the active tunnel but the traffic didn’t failover and tunnel 2 didn’t learn the route
Hello, thanks and glad you found it useful.
No, I haven’t tried active/active but last I checked each VNET could only have a single VNG. This would mean you need to create a second VNET/Virtual Network Gateway in Azure, peer them and create a connection from the second VNG to AWS. Transitive routing should then work. Is that what you tried?
I created two local network gateways and Azure says they are connected but AWS only indicates the firts IP is BGP and the other tunnel is up (but really DOWN as well) but not BGP so as D Hermans says when try to take the first link down there is not failback, the only nice thing about BGP this way is there is not need to add routes manually but does not work with both AWS active, for normal VPN without BGP using both IPs down AWS makes both tunnels up
Until Azure has the ability to set individual APIPA ranges per tunnel, rather than per Virtual Network Gateway, this might not work as expected with two tunnels.